Preventive Security vs Detective Security Making Your Workforce a Formidable Preventive Security Control
Starting with a quote, “an ounce of prevention is worth a pound of detection” prevention is always seen as better than cure, of course we hear this mostly in medical related usages. The same concept can be applied to information security too.
Have a good look at some legacy technologies such as antivirus. They do not prevent from a virus infection but only notify the detection of the infection. Wouldn’t it be too late if your antivirus detects a malware in your computer after the malware has corrupted your files and stole sensitive information? What about the cost of cleaning up the malware (an act also known as corrective action)? In many cases the cost of malware infection is not only directly related to physical damages but also non-physical damages such as tarnished brand name, loss of business opportunities & etc.
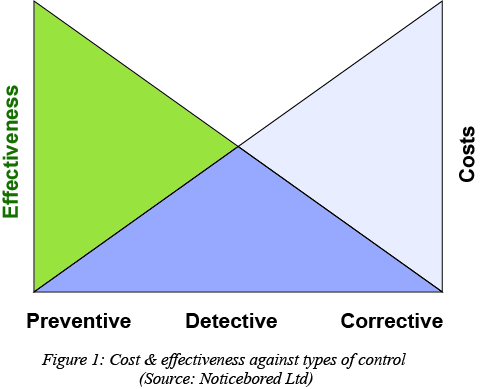
Figure 1 above demonstrates how preventive based security control results in higher efficiency whereas detective / corrective based security control can be very costly. As a general guideline, security controls designed to prevent breaches from ever occurring are more cost-effective than those designed to identify or correct one.
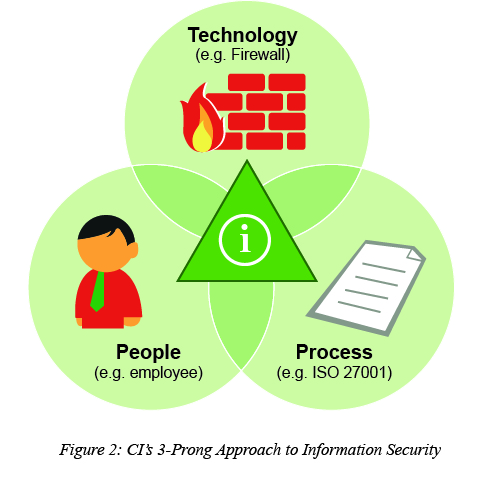
One of the key preventive security measures is addressing the human layer. As a matter of fact this can be regarded as the most important component of information security ecosystem. More often than not, organizations ignore the importance of this layer and concentrate on deploying technology and process based security controls only. CyberIntelligence is a very strong advocate of human layer security and that is why we use a 3-prong approach of PEOPLE – PROCESS – TECHNOLOGY (as depicted in Figure 2 below) in addressing information security needs of organizations. Without any one of these components, an information security initiative is destined to fail.
Trust us when we say that humans are the weakest link in information security. Let’s look back in the last 2 years and analyze most of the security incidents that happened. Large percentage of the incidents was due to human factor. As a matter of fact most of the high profile cases such as attacks suffered by RSA and Coca-Cola were all due to humans. Attacks against human layer are easier than attempting to penetrate into a highly secured perimeter security of a company because humans are gullible, greedy, curious and can be easily deceived. Clearly knowing this most of the hacker groups are channeling their energy and effort to exploit the vulnerabilities of human layer by means of social engineering attacks
So how do we tackle this issue? The answer is simple even though the execution itself may not be that simple. This human layer related issue can be tackled by developing and delivering a powerful information security awareness program that can increase the information security awareness level and at the same time change the mindset and behavior of the workforce. Addressing the human layer is a great preventive security measure. Which one do you prefer? – deploy a security technology and hope that your users will not click on links in phishing emails or deploy a security technology and teach your users how to identify a phishing email and why not to click on the links?
Understanding that security awareness and security behavior are two different things and both have to be addressed appropriately is the key. Let’s take a car driver as an example: A driver may have a very high awareness level of the road safety rules and regulations but that does not make him/her a safe driver because that part is entirely dependent on his/her behavior on the road.
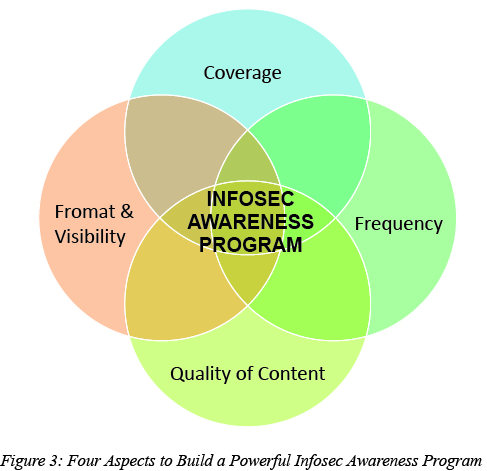
Moving on to build a security awareness program, figure 3 above shows four key aspects that need to be considered. Convergence of all four aspects will result in a powerful information security awareness program. Missing any one of the aspects will reduce the impact of a security awareness program. The four aspects are further elaborated below:
1. Coverage – Identify the target workforce and tolerable deviation
2. Format & Visibility – The format must be suitable for the target audience; i.e. verbal / electronic / paper and visibility is the channel through which the content is delivered; i.e. classroom trainings / e-Learning / posters / surveys / social media / emails.
3. Frequency – The gap between two awareness deliveries and the gap should be minimal (because awareness should be a continuous program). Take note that different people have different learning capacity.
4. Quality of Content – The content should show the impact of poor security practice, must be relevant to business, clear and concise.
If all the above sound a little too much of work, we at Cyber Intelligence have just the solution for you. Our masterpiece offering called Security Vitamins will take care of your security awareness initiative in your organization whereas you can focus on your core business. A typical one year information security awareness and competence management package contains the following:
a. 1 induction video
b. 12 short videos
c. 6 screen-savers
d. 6 newsletters
e. 6 digital posters
f. 1 session of behavior assessment
Please visit www.cyberintelligence.my/securityvitamins for more information.